Setting Up Identity Federation in plusserver S3
3 minute read
You have the option to configure identity federation if you want to use groups and users from another system such as Active Directory, OpenLDAP, or Oracle Directory Server. This allows for seamless integration of your existing user and group management into the StorageGrid system, thus enabling your employees to use their familiar credentials to access plusserver S3 without having to manage separate credentials. Not only does this simplify administration, but it also enhances the security and user-friendliness of your plusserver S3 environment.
Our documentation will guide you through the process of setting up identity federation so you can quickly benefit from the advantages of this integration.
Step 1: Log in to the plusserver S3 Customer Portal
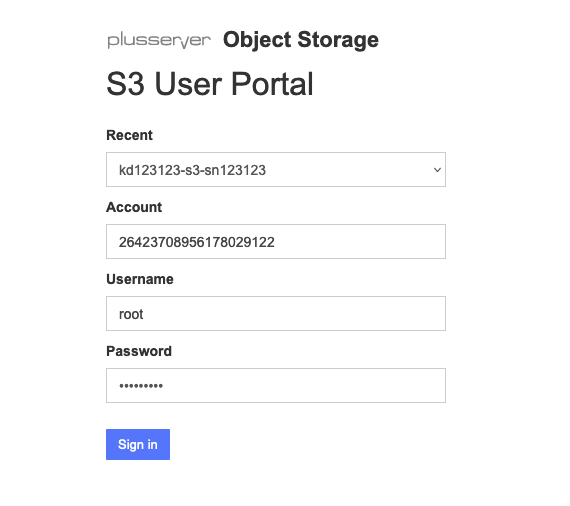
- Open your web browser and visit the following website: plusserver S3 Portal.
- Use the provided user credentials (you can find them in the plusserver Customer Portal under “Contracts and Billing” → Select S3 contract → Access Data → “Show Credentials”) to log in. The username is “root”. Please use your personal password to proceed. The Account ID is also displayed here.
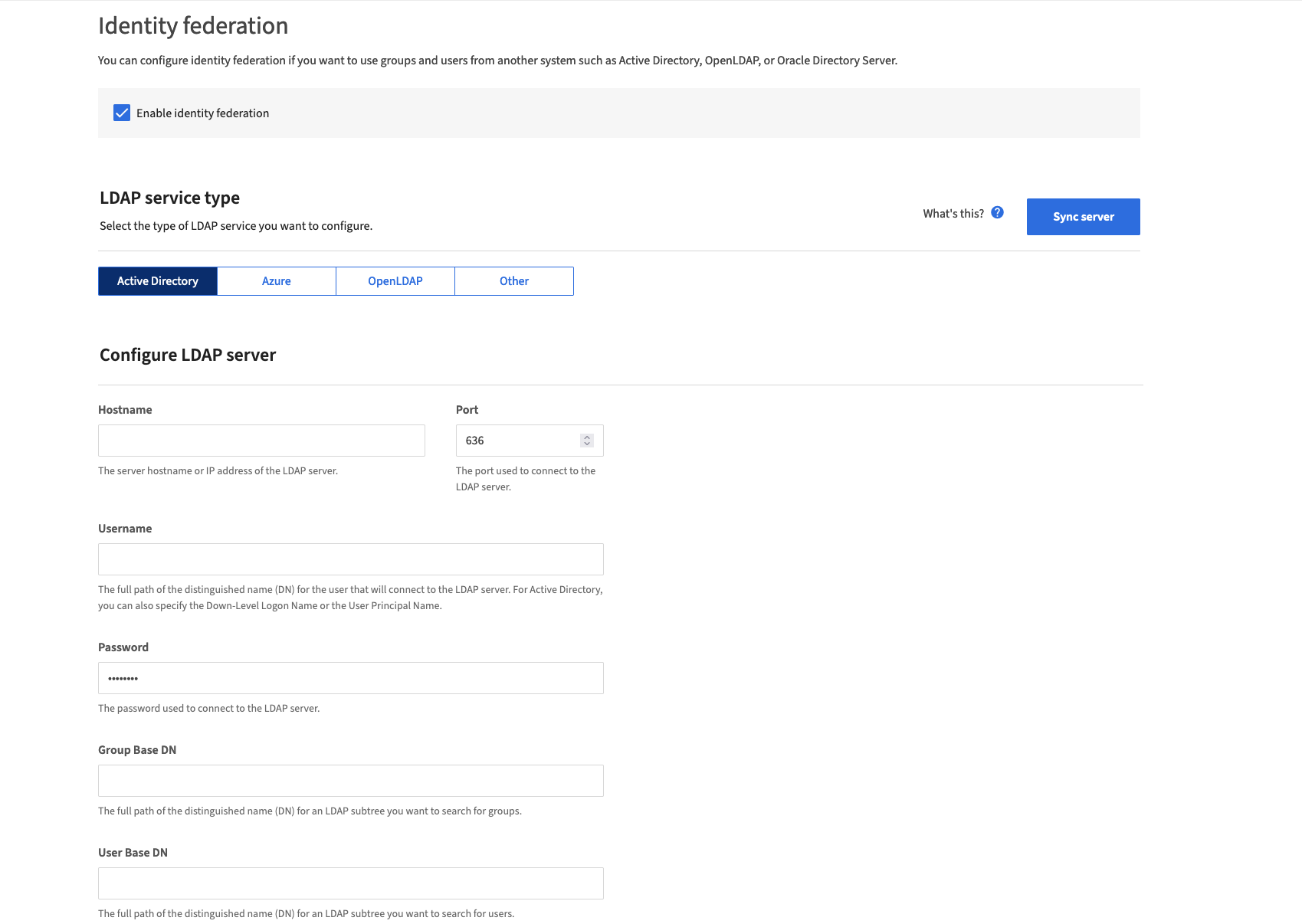
Step 2: Set Up Identity Federation
- Click on “Access Management” on the left side and choose “Identity Federation.”
- Here you have the choice between Active Directory, Azure, OpenLDAP, and Other.
- You can then test the connection and save it.
Now you are able to use identity federation.
Step 3: Create a Group
To grant appropriate permissions to your users, you need to create a group first. Follow these steps:
- Click on “Groups” on the left side.
- Select “Create Group.”
- In the group creation interface, choose the “Federated Group” tab.
- Assign a unique name for the group. This name must be set according to the identity source. Please use the following guidelines:
- Active Directory: Use the “sAMAccountName” attribute.
- OpenLDAP: Use the “CN” (Common Name).
- Other LDAP servers: Determine the appropriate value for the unique name that corresponds to the LDAP server used.
By following these steps, you define an identity federation group derived from your identity federation. This group will serve as the central mechanism to assign users the appropriate access permissions to your resources.

Info
If you want to create and manage users and groups via identity federation, it is important to consider this in bucket or group policies.
Here is an example of how you could create a policy for a bucket to grant access to only a specific user:
Example:
{
"Version": "2012-10-17",
"Id": "UserBucketPolicy",
"Statement": [
{
"Sid": "AllowUserAccess",
"Effect": "Allow",
"Principal": {
"AWS": "arn:aws:iam::ACCOUNT_ID:user/USERNAME"
},
"Action": "s3:*",
"Resource": [
"arn:aws:s3:::BUCKET_NAME",
"arn:aws:s3:::BUCKET_NAME/*"
]
},
{
"Sid": "DenyOtherAccess",
"Effect": "Deny",
"NotPrincipal": {
"AWS": "arn:aws:iam::ACCOUNT_ID:user/USERNAME"
},
"Action": "s3:*",
"Resource": [
"arn:aws:s3:::BUCKET_NAME",
"arn:aws:s3:::BUCKET_NAME/*"
]
}
]
}